What do Spoofing, Whaling, and Phishing have in common? They are all scams that utilize email and rely on the recipient being convinced to take a specific action.
Spoofing
Email spoofing is someone (or a machine) that sends emails pretending it is from someone else. It can trick a user into thinking it is from the email hosting provider and/or sender, but that isn’t the case. See example below:
Most of these are phishing attempts to collect sensitive, personal information from the email recipient. Many of these emails include a link, requesting that the recipient click the link to reactivate or restore their email account. This will never be the case & these are NOT legitimate emails.
If you receive an email that appears to come from someone you know or any other official looking email, but seems “off” because of it’s content, timing, phrasing or anything else it’s requesting of you, do not click on any links within the email, download any attachments, or provide any personal information.
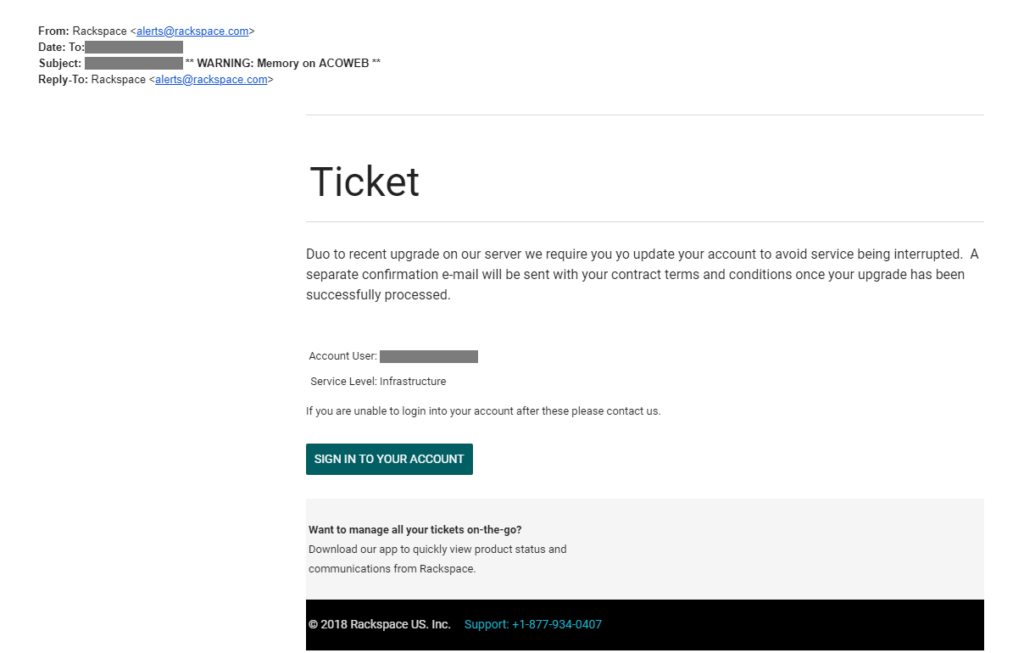
Phishing
Phishing is an email scam targeting an individual, but on a larger scale, millions of people receive one or more of these every day. Phishing emails tend to focus on tricking someone into clicking on a link and entering a username, password, or other information that is tracked or entered into a non-legitimate website.
Unfortunately, phishing attempts in general are on the rise. Here are a few reminders about best practices with email:
- If ever in doubt (phishing, whaling, spoofing), pick up the phone and talk to the person sending to see if the action being requested via email is legitimate. Clients can always call us with questions or concerns.
- Do not share personal information via email.
- Double-check that any attachments are from a legitimate source before downloading. If you’re not expecting an attachment, do not open it.
- Watch for suspicious content and misspellings.
- Avoid clicking links from within an email.
- Spoofing and phishing emails will often contain words the evoke emotion and quick action like: Flagged, Violation, Urgent, Reactivate Account, Scheduled for Deletion, Cancel Deactivation, and Disabled.
- Be suspicious of emails that claim to be urgent or pose any unusual requests.
Read more about phishing here.
Whaling
Whaling is when an email scam attack is made toward the heads of companies, other highly-ranked individuals at a company, or someone with access to bank accounts and finances. These types of scams often appear to take place between one person in a company asking another to pay a bill, transfer money in accounts, etc.
As always, we’re here to help our clients move their digital marketing forward with confidence. Call or email us with questions or concerns.
